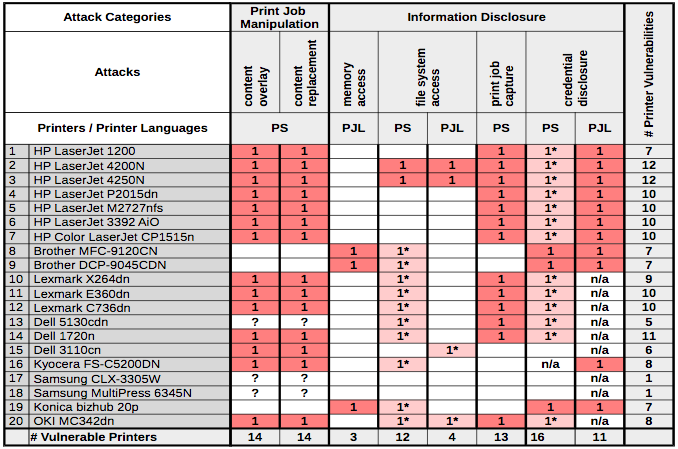
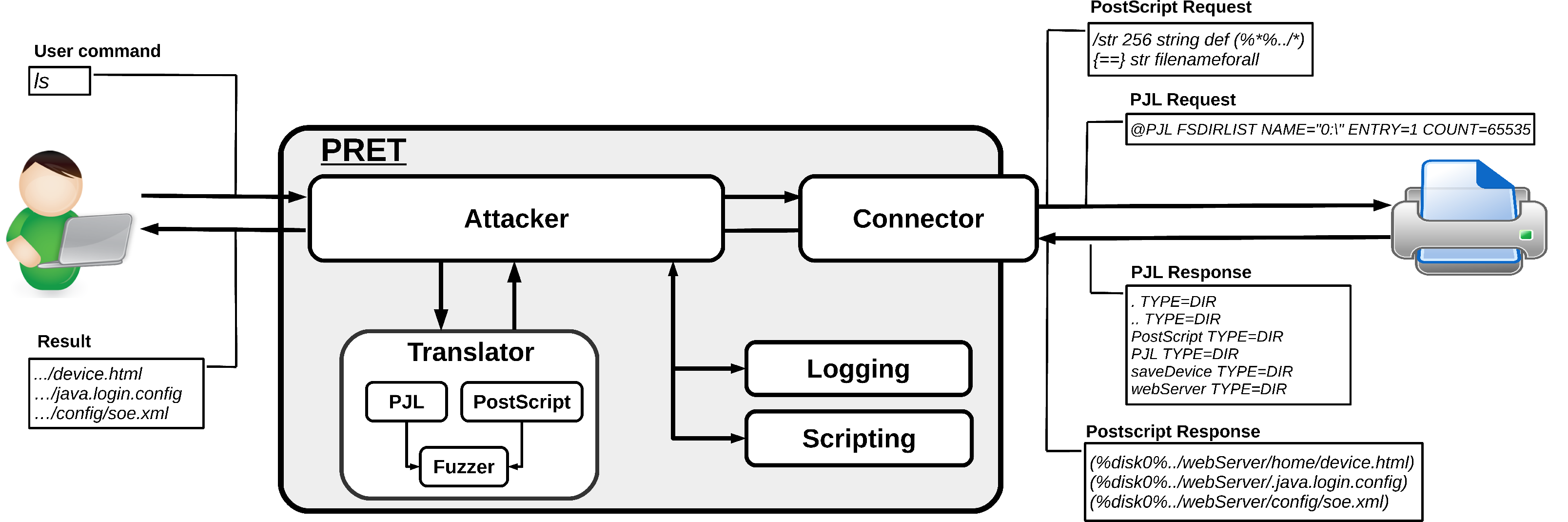
☣ KitPloit - Hacker Tools on Twitter: "PRET - Printer Exploitation Toolkit https://t.co/gY1nGylnP4 #Capture #Cheat #Database https://t.co/3R1K5HgBWz" / Twitter

Strategies to End Commercial Sexual Exploitation of Youth: A toolkit for collaborative action | National Center for Youth Law

Insights from the PewDiePie Hack: Trends in Strengthening Public Sector Printer Security – Connected IT Blog


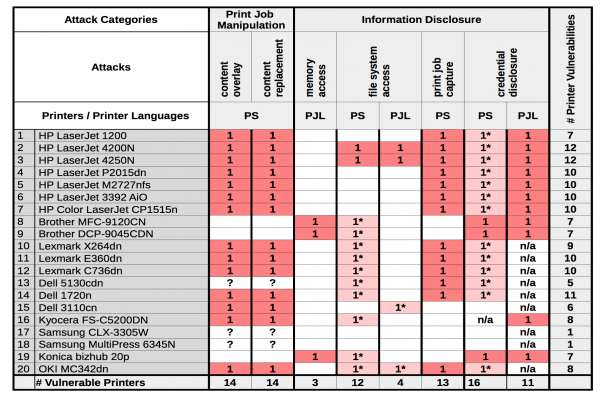

![How to Hack and Exploit Printers in Seconds - HackingPassion.com : root@HackingPassion.com-[~] How to Hack and Exploit Printers in Seconds - HackingPassion.com : root@HackingPassion.com-[~]](https://hackingpassion.com/how-to-hack-and-exploit-printers-in-seconds/featured-image.png)